
Once considered a luxury for the tech-heavy, or cybercriminals with something to hide, virtual private networks (VPNs) have come to a claim a regular spot in the average person’s privacy toolkit.
Over the last decade, incident after incident has proven the need for the everyone to become more privacy conscious. Consumers have learned that never has their privacy been under more risk. And the VPN market has blown up as a result.
VPNs serve other purposes too. For many, they help them access content that’s otherwise blocked in their location, such as Netflix or even Facebook. For others, they simply want to ensure their security while visiting volatile public networks, or when dealing with sensitive personal information.
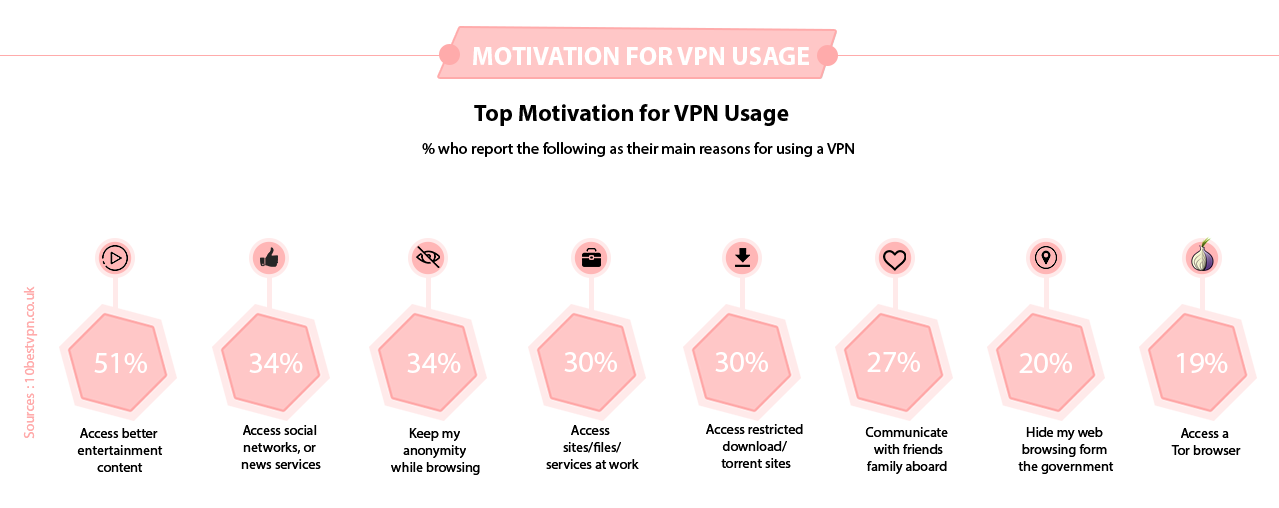
As VPNs have grown in popularity, more players have entered the market. It’s no surprise, then, that the VPN industry has continued to grow apace, and is expected to be worth 35 billion dollars in 2022 at its current growth rate.
With premium VPNs coming at some cost, millions have now turned to free VPNs in order for their obfuscation, unblocking, and privacy needs to be satisfied at no cost.
But should you be joining the bandwagon of free VPN users? Studies on free VPNs by researchers from the University of California has proven that most free VPNs do not live up to their billing. In fact, users who adopt these VPNs may be exposing themselves to even more danger.
Having analyzed different free VPNs, researchers came to the same conclusion we’ve reached. Many free VPNs:
Back in July, it emerged that 7 free VPNs – UFO VPN, Rabbit VPN, Free VPN, Fast VPN, Flash VPN, Super VPN, and Secure VPN – which all lay claims to a strict no logs policy, had left private user data exposed.
This breach affected an estimated 20 million VPN users who had both their browsing activity, and other Personally Identifiable Information (PII) exposed, researchers at VPNMentor found.
Going by their advertised no-logs policy, these VPNs aren’t supposed to even have this data stored in the first place. But they did.
Stored logs included everything from email addresses to actual addresses, clear text passwords (the high stakes encryption promised should prevent the appearance of your password in plain text), IP addresses, device type and ID, Internet Service Provider (ISP), payment details, sites visited, and the server’s users connected to.
Even worse, all of this data was completely exposed. As researchers would find, these VPNS had left their servers open to any who probe, with no form of encryption whatsoever.
Far from surprising, this find is in line with other research findings. In a study conducted in September, ProPrivacy tested about 204 free VPNs on the Google Play Store and found that 40% of the free apps were leaking PII of their users due to a lack of IPv4 address, or a lack of protection on IPv6 connections.
Interestingly, 18% of analyzed VPNs were found by University of California researchers to have tunneling protocols devoid of any encryption. Despite their promise of complete online anonymity, these free VPNs left internet traffic just as exposed as the traffic of non-VPN users.
For VPNs, the lure has always been about protection. Whether a VPN leaks data due to poor encryption techniques or there’s simply no encryption protocol whatsoever, the VPN offers no protection to its users.
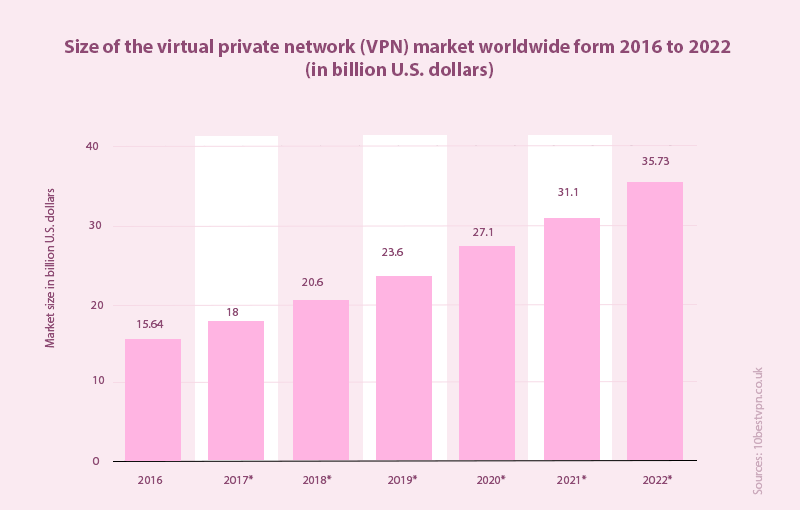
The latest internet protocol system IPv6 was considered a dream come true for many in the tech world. Not only was it to expand device support into the hundreds of trillions, it also introduced a tougher, more secure 128-bit addressing scheme.
As with everything this big, its adoption across the internet has been slow. Many websites have remained with the original IPv4 protocols with which they were setup, and devices have continued to use this connection system.
Still, IPv6 is gaining in its adoption levels. Google’s data places current adoption levels at about 30%, as of this writing. This number can get much closer to 35% on weekends as internet usage shoots up.
Premium VPNs recognize the need to also tunnel this traffic, as well as the need to provide leak protection for this traffic.
Some proceed, instead, to disable IPv6 at system level, ensuring connections are only possible in the IPv4 protocol they can encrypt. Either way, every connection type is addressed and secured.
The tests mentioned above noted that about 40% of the free VPNs on Google Play Store either failed to provide an IPv4 address, or leaked data through the IPv6 or WebRTC channels.
In fact, many of these apps had completely failed to address the new and increasingly adopted IPv6, likely excusing it for its lack of popularity.
In their own research, University of California researchers found that about 84% of free VPNs pulled at random did not tunnel IPv6 traffic through their encryption interface, while 66% did not tunnel DNS traffic.
These are hugely concerning as there’s no telling which connection system the website you’d be visiting will employ. A lack of encryption for IPv6 protocols means you could surf the internet completely unprotected by your VPN, if every website you visited ran on a IPv6 protocol.

Some free VPNs were found to go beyond just compromising privacy. These VPNs went one step further to turn devices into a minefield which could be used to exploit and manipulate users in many different ways.
About 38% were adjudged to contain some form of malware; 82% require permissions to access sensitive personal data; and, 16% adopted an unmentioned peer-forwarding system for traffic tunneling, rather than the typical VPN server, thus exposing users to many potential and unstated risks.
Another 16% of those analyzed fraudulently modified HTTP proxies from user traffic in order to inject advertising code, with some going so far as to redirect traffic to advertising partners. And, a number of them were found to selectively intercept traffic from banking, ecommerce, social media, and email sites.
For the VPN user, this means that the app you’ve downloaded to protect your privacy and ensure your online security, could be actively involved in compromising your device and exploiting your personal data.
The Play Store is disturbingly littered with VPN apps of different names by the same developer. These VPNs adopt the same infrastructure, and link you to the same IP addresses, but try to target different markets using different names.
The two biggest developers we found culpable were Softtechstudio and REIKO VPN DEVELOPER. Softtechstudio boasts a whooping 30 VPNs under its name, all of which adopt a country name as though they were built specifically for that country.
Note that premium VPNs do not need this distinction to successfully target any local market. CyberGhost, for instance, boasts over 6,000 servers in different countries across the world, and is widely acclaimed for its worldwide protection despite all of its servers being under one app.
The second, REIKO VPN DEVELOPER, more than doubles the number of Softtechstudio’s VPN apps. Unlike Softtechstudio, these aren’t disguised as being country-specific. They’re just named differently, as though they were all different.
These VPNs share similarly minimal descriptions, and boast a strikingly similar user interface. On some occasions, slight adjustments were made to the user interface, but these were rare and minimal.

These apps were far from alone, though, with over 70 app developers noted to have multiple apps under different names.
Interestingly, there’s also a good number of VPN apps developed by a single developer and subsequently white-labeled to other companies.
They do not share the same developer name, but may look incredibly alike, boast the same VPN infrastructure, and typically work with the same servers.
The seven VPNs mentioned earlier make for a great example. All seven share the same server, which is enough reason for concern. Interestingly, four of them also carry very similar website designs, as seen below.
The data left exposed by the 7 interrelated, but supposedly different, free VPNs amounted to about 1.2TB. This was spread over more than 1 billion stored records, and affected an estimated 20 million-plus users.
Using the total number of downloads per app, we estimate that upwards of some 40 million users may have been affected by VPNs noted to leak PII data in one form or other.
Should you throw in all the other forms of device compromise and possible data theft discussed above, the number of downloads just about doubles to over 80 million. This is huge by any standards.
The online world is rife with hackers and cybercriminals, many of whom are always on the prowl for the latest victim. It’s also almost impossible to tell if the app developers themselves are attempting to use this data for nefarious purposes. Unfortunately, even if they aren’t, there’s no telling into whose hands this data will be falling.
Following any data leak, there are a number of possibilities that could follow:
 Fraud, Extortion and Blackmail
Fraud, Extortion and Blackmail With a user’s personal details exposed, there’s no shortage of opportunities to the savvy hacker. Hackers could attempt to engineer passwords to sensitive accounts using combinations of the leaked password and email address.
In a world where many choose to use the same – or very similar – passwords for multiple accounts, this is a potentially very disastrous outcome.
Where unsuccessful, hackers could have yet another go through phishing schemes. Armed with the email address, home address, and browsing data, a cybercriminal could create an effective phishing campaign that’s very specific to the targeted user.
Mimicking a real business, phishing campaigns attempt to trick victims into providing hackers with sensitive data like their credit card details. A phishing campaign could also nudge victims towards opening links with dangerous malware and viruses.
Users whose personal activities are exposed by a VPN could also become victims of extortion or blackmail. Cybercriminals could hold them to ransom, threatening to expose their private activities to colleagues, family, friends, or even the government, except a substantial amount is paid.
Consider the many free VPNs in the Android ecosystem which require access to sensitive personal data like text messages, also. Then imagine what would happen when the vulnerabilities of these apps expose this data to hackers with malicious intent.
Unfortunately, there’s no guarantee that a one-time payment would make blackmail stop. Malicious criminals could turn such sensitive information into a gift that never stops giving.
Whichever the case, there’s no denying the grave impact this would have on victims. Everything from their finances to their mental health and personal lives could be drastically affected. Given the economic uncertainties of these times, there could be a multiplier effect to the consequences.
 Prosecution and Arrest
Prosecution and Arrest To understand the possibility of arrest or prosecution on VPN users, we took a closer look at the demographic for VPN users. Contrary to what you might believe, the US doesn’t have a large percentage of VPN users to internet users.
Instead, the win here is within countries with very repressive, or somewhat repressive governments. Per the Global Web Index, VPNs are most popular in Indonesia with 55% of internet users using a VPN last month. Although VPNs remain legal in the country, sites like Netflix, Vimeo, and Reddit are blocked.
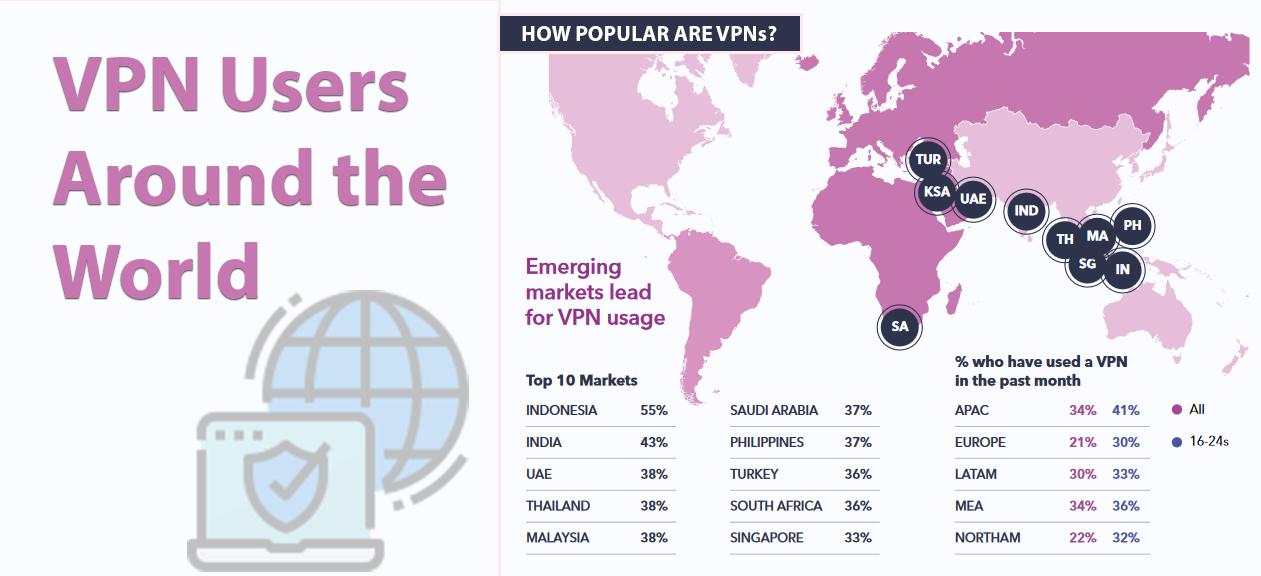
Like Indonesia, most of the countries topping the list do not have outright bans on VPNs. However, with content censorship quite high within these countries, there are grounds for potential arrest and prosecution should your activities while using a VPN be exposed.
Then again, there’s also Turkey – with 36% of internet users using a VPN – where VPN usage is completely under ban. Identified VPN users are thus easily marked as persons of interest, with punishments ranging from simple fines to possible arrest and detention.
By recording user’ activities, logging their personal data, leaving their networks or servers unencrypted, or having very weak encryption protocols, free VPNs expose vulnerable users – users who have turned to a VPN for the very protection they now betray.
Should you choose to use a VPN for any reason, it is your duty to ensure you’re fully protected. Of course, every technology can fail, and even the most secure of VPNs today may someday be hacked.
 Avoid free VPNs
Avoid free VPNs Your first task when selecting a VPN is ensuring your risk index is very low. VPNs that keep no PII data, for instance, expose you to very little risk even when breached.
There are, no doubt, some excellent free VPNs for Windows or Mac on the market. We’ve also taken the time to identify some top free VPNs for Android, which can also be downloaded on the Play Store.
But even these VPNs all come with their limitations. Sometimes, this could be in the form of popup ads, frustratingly slow server speeds, softer encryption protocols, or bandwidth limitation.
Unfortunately, stepping out of this class of free VPNs, and into those that promise everything with no limitations can be harmful. A lot of them compromise your security, exposing you to the same risks that got you involved with them in the first place.
 Do your due diligence
Do your due diligence Should you choose to work with a VPN, it’s important that you take the time to carry out your due diligence. Check out the reviews of the app, with particular focus on the negative reviews. Look out for expert analysis on the app, and note what the critics are saying.
When reviewing user and expert reviews, pay particular attention to what is said about the VPN’s security protocols, not just its speed.
Unfortunately, VPN leaks can be a tad too difficult to discover. Hundreds, even thousands, could use a VPN without detecting personal data leaks. This could leave a VPN with a 100% rating on Play Store for its ease of use and functionality, despite being a security hazard.
 Get a reliable VPN
Get a reliable VPN To avoid any potential risks and stay fully protected online, consider purchasing a more reliable premium VPN. Although they can be quite pricey, many of them offer much cheaper pricing on longer term deals.
Of course, even within the premium market, not everything is as it seems. We’ve identified some of the best VPNs of 2022 here, so you don’t have to search so hard. This includes crowd favorite CyberGhost, and security juggernaut NordVPN.
Because you’d be paying for these VPNs, the providers will be at your service. This means availability for questioning and assistance-rendering. They’d also be at pains to protect the data you’ve paid them to protect, and are certain not to sell this data.
Our mission is built around helping you stay safe online. This is why we’ve built the DNS Leak Test Tool to help you test for leaks all by yourself. Tests can be run at the drop of a hat in a matter of seconds.
A precise and independent tool, the Leak Test tool allows you test for DNS leaks regardless of your technological knowledge. Simply visit the web page after connecting to a VPN to confirm your online address. If the page reveals your true location, your VPN is clearly not strong enough.
However, if after running it the page reveals a location associated with your connected server, your VPN is giving you the right protection.
If you really desire complete online protection, stay away from free VPNs. Although these are great money saving options, they are also more likely to leave you exposed.
Using a compromised free VPN is exactly what was meant by the saying: ‘from frying pan and into the furnace’. Security concerns, ad pop-ups, slow connections, and restricted bandwidth are all a part of the package with most free VPNs.
Rather than go for a free option, seek out cheaper premium options like Surfshark. These are faster, more secure, more private, and solid enough to unblock websites and give you a wholesome online experience.